Hide your IP address to stay anonymous. However what many of these techniques effectively boil down to is an ever-evolving family of hacking strategies known as phishing.
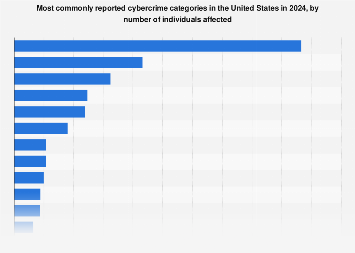
Most Frequently Reported Types Of Cyber Crime 2021 Statista
Internet in India began in 1986 and was available only to the educational and research community.

. Venafi cloud service important please read carefully before continuing with registration andor activation of the venafi cloud service service. Therefore you will not encounter cyber. AIR Spotlight - Indias Role in the United Nations.
Human trafficking slavery and slavery-like practices such as servitude forced labour and forced marriage are complex crimes and a major violation of human rights. The computer may have been used in the commission of a crime. Cybersex trafficking live streaming sexual abuse webcam sex tourismabuse or ICTs Information and Communication Technologies-facilitated sexual exploitation is a cybercrime involving sex trafficking and the live streaming of coerced sexual acts andor rape on webcam.
Browsers verify downloaded files. General public access to the internet began on 15 August 1995 and as of 2020 there are 71874 million active internet users that comprise 5429 of the population. We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits.
Samsung Engineering signs an agreement with Aramco for the National EPC Champio Samsung Engineering one of the worlds leading engineering procurement construction and project management EPCPM companies announced today that it has signed an agreement with Aramco for the National EPC Champions initiative. Since that time the definition of identity theft has been statutorily defined throughout both the UK. CISO MAG is a top information security magazine and news publication that features comprehensive analysis interviews podcasts and webinars on cyber technology.
They are commonly referred to as an internet-based collective of hacktivists whose goals like its organization are decentralized. Banco de sabadell sa. Robbery is the crime of taking or attempting to take anything of value by force threat of force or by use of fear.
Around the world men women and children are trafficked for a wide range of exploitative purposes such as. Encrypt your data to prevent cybercrime. Read about the amendments of the Indian Constitution Article 368 constitutional amendment process and also the source of amendability.
As of May 2014 the Internet is delivered to India mainly by 9 different undersea fibres including SEA-ME-WE 3. Scroll to the bottom to accept. What are the Categories of Cyber Crime.
In the course of 2022 the Health Protection Command of the Carabinieri Corp enforced 61 orders issued by the competent directorates general of the Ministry of Health providing for the shutdown of websites selling different types of prescription-only medicines in breach of the existing legislation. Three are three types of amendments in the constitution. Tony has worked as a Project and Program Manager for almost 30 years with a particular focus over the last 7 years on delivering strategic cybersecurity capabilities in Australia USA England Austria South Africa Singapore Malaysia Hong Kong and Thailand.
The official signing occurred on July 5. Join the fight against malicious programs and cybercrime on our Computer Science Cyber Security MSc. A9Play is one of Malaysias top and trusted live gambling apps with advanced technology that combines all games in a single app.
Leverage our proprietary and industry-renowned methodology to develop and refine your strategy strengthen your teams and win new business. Cybersex trafficking is distinct from other sex crimes. Based on each category of cyber crime cybercriminals use different levels and types of threats.
Banco de la nacion. Banque al wava mauritanienne. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply.
Most of the best ones use AES 256-bit encryption which is the same standard used by banks governments and militaries. Hacking and other types of cybercrime. Cybercrime is a crime that involves a computer and a network.
Different types of high-tech crime may also include elements of low-tech crime and vice versa making cybercrime investigators an indispensable part of modern law enforcement. Other examples of trending cybercrime include fake parcel delivery services to acquire personal information sextortion scams that prey on the targets guilt and social standing and ever-classic tech support scams. Kenyan President Uhuru Kenyatta signed a bill May 16 2018 criminalizing 17 different types of cybercrimes including cyberbullying espionage and computer forgery.
Vietnam technological and. Identity theft occurs when someone uses another persons personal identifying information like their name identifying number or credit card number without their permission to commit fraud or other crimesThe term identity theft was coined in 1964. Methods of cybercrime detective work are.
That is it is a larceny or theft accomplished by an assault. This Day in History 04 Sep 1825 Dadabhai Naoroji Birth. As the theft of.
Get 247 customer support help when you place a homework help service order with us. Virus-infected files and malicious trojans are established malware types and developers have various defensive detection and mitigation techniques to defend against them. Topic of the Day Cybercrime.
And security software can scan files to be written read andor executed to. Anonymous is a decentralized virtual community. A9Play offers an unlimited number of games and opportunities with discount offers making it the best and reliable gambling site.
In computing a denial-of-service attack DoS attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a networkDenial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an. First national bank of swaziland. Cybersecurity acts as a driver for national economic social and defence interests.
Cyber crimes are categorized into three broad categories individual property and government. Saigon thuong tin commercial joint stock bank. Victims are transported by traffickers to.
Anonymous seeks mass awareness and revolution against what the organization perceives as corrupt entities while attempting to maintain anonymityAnonymous has had a hacktivist impact. And misinformation made the. According to common law robbery is defined as taking the property of another with the intent to permanently deprive the person of that property by means of force or fear.
Hong leong bank berhad. VPNs use encryption to scramble your traffic so that no one can intercept and exploit it. Bigpay malaysia sdn bhd.
Applications need approved permissions before installation. We will give you the skills you need to become a Cyber Security and Digital Forensics professional intercepting collecting analysing and reporting the events in cyberspace and digital media. There are different types of cyber crimes that use malicious code to modify data and gain unauthorized access.
Servitude Slavery Forced labour Debt Bondage Forced marriage or Organ harvesting Australia is primarily.

Cybercrime Vs Traditional Crime Techniques A Comparison

Cybercrime The Dark Side Of Entrepreneurship
Cybercrime Which Ones Are The Most Common Threats Today Red Points

What Is Cybercrime Different Types And Prevention

Philippines Cyber Crimes Incidents Within Region 7 By Type Statista

Cybercrime Which Ones Are The Most Common Threats Today Red Points

Causes Of Cybercrime And Preventive Measures Krazytech

The 10 Worst Cyber Crimes Analysed

Singapore Rate Of Cybercrime 2021 Statista
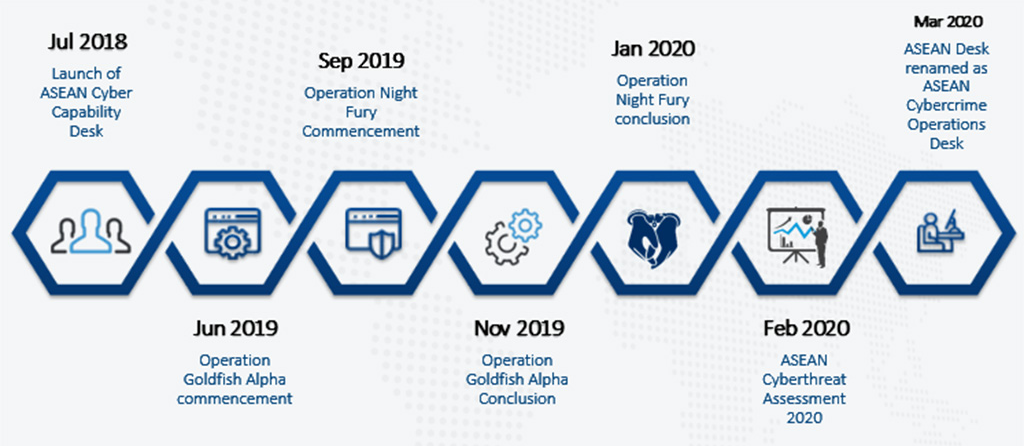
Asean Cybercrime Operations Desk
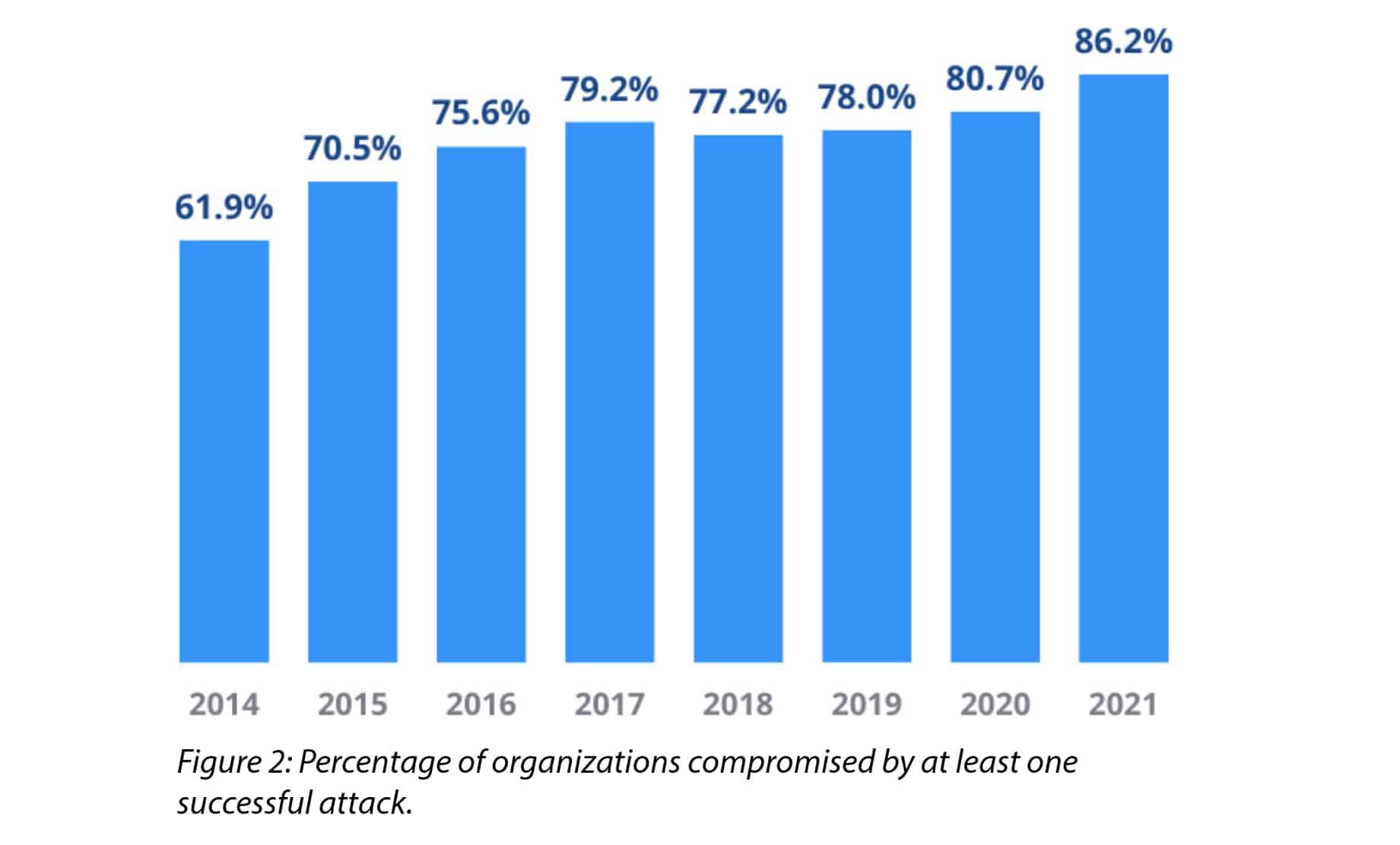
300 Terrifying Cybercrime Cybersecurity Statistics 2022
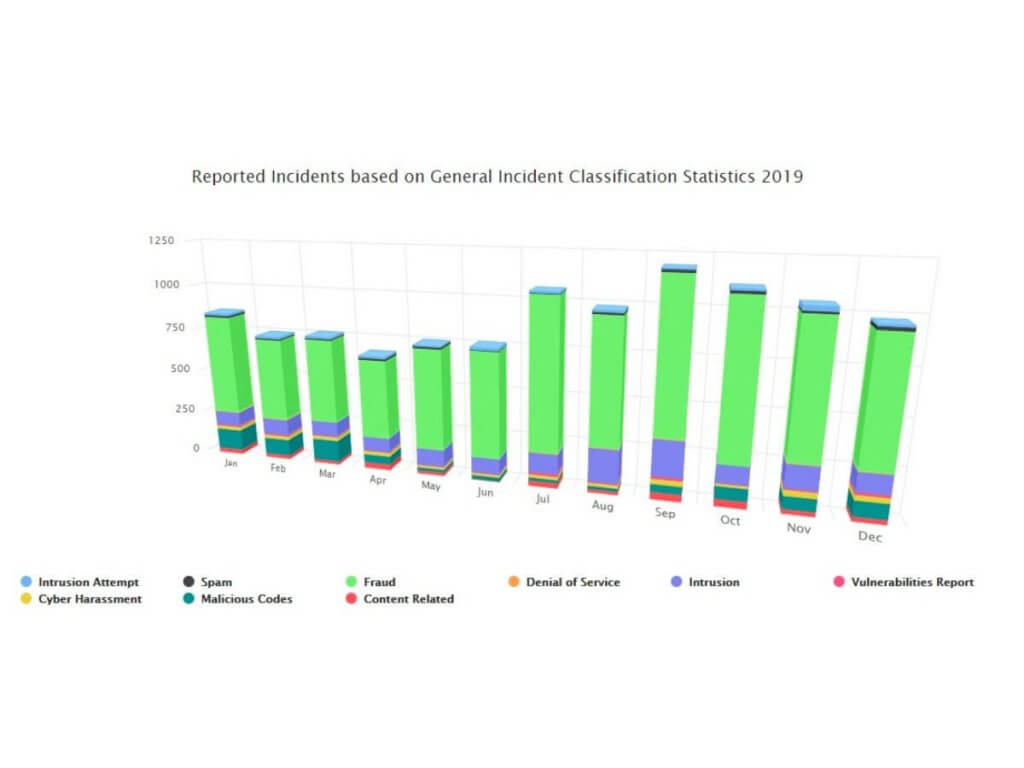
The True Cost Of Cyber Crime In Malaysia Spectrum Edge

This Infographic Shows The State Of Encryption Today Encryption Infographic Infographic Encryption

Types Of Cybercrime Panda Security Mediacenter

Zeus Malware Double Threat How To Defend Yourself Against Zeus P1networks More Info Https Storify Com P1ne Malware Cyber Security How To Defend Yourself

Cybercrime Today And The Future
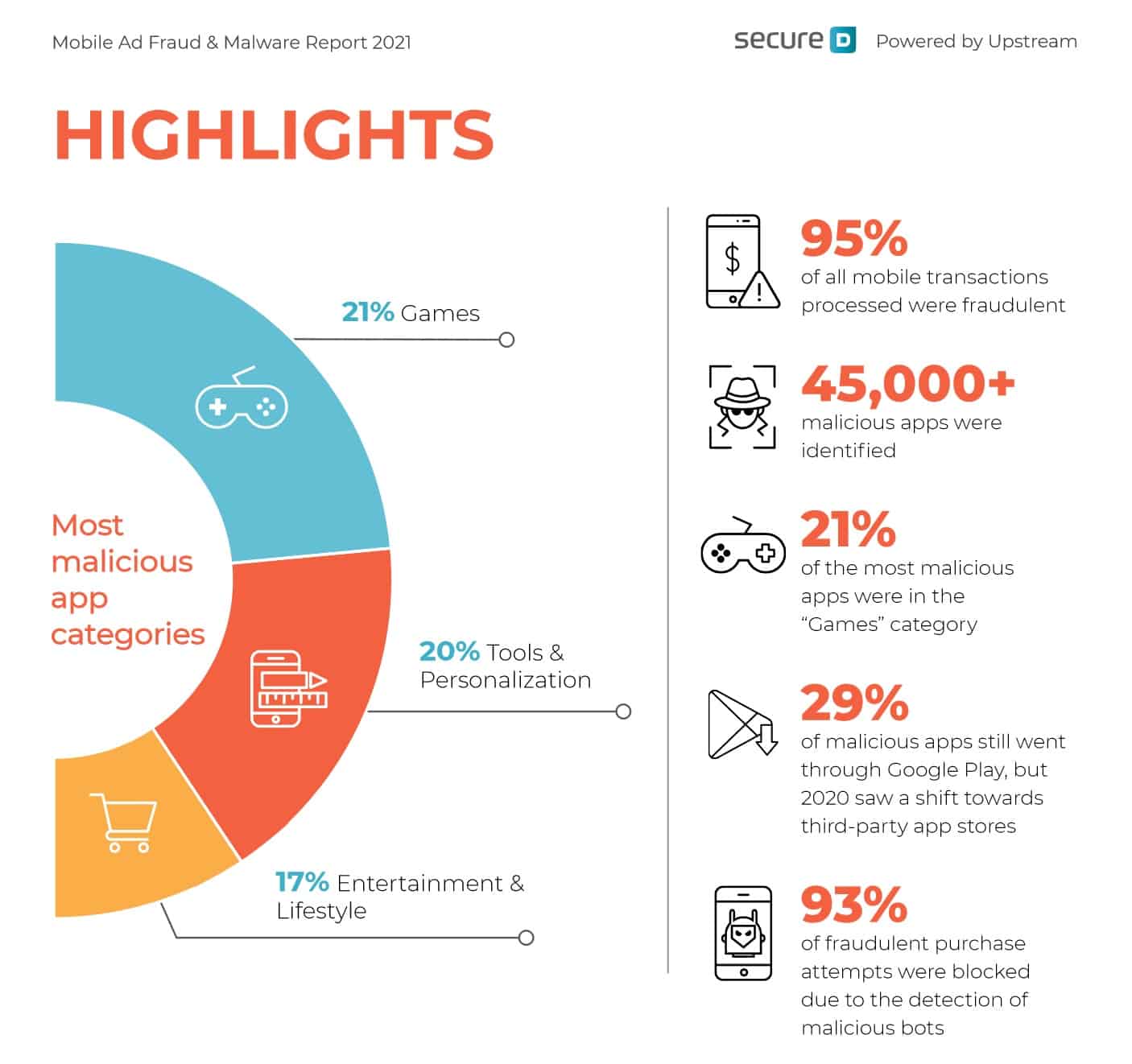
300 Terrifying Cybercrime Cybersecurity Statistics 2022


